Managing Configuration and Secrets
Managing Configuration and SecretsWhere things areListing All ConfigMapsViewing ConfigMap ValuesViewing Secret ValuesAdding and Updating Values
Our deployment strategy separates configuration and secure data from the codebase. You'll be familiar with this from the previous Preparing your Repository booklet, which had you putting all this data into a separate env/ folder.
This separation is maintained in Kubernetes, using the ConfigMap and Secret objects described in the introduction. The files and folders in your env/ folder correlate to different ConfigMaps and Secrets, as shown below.
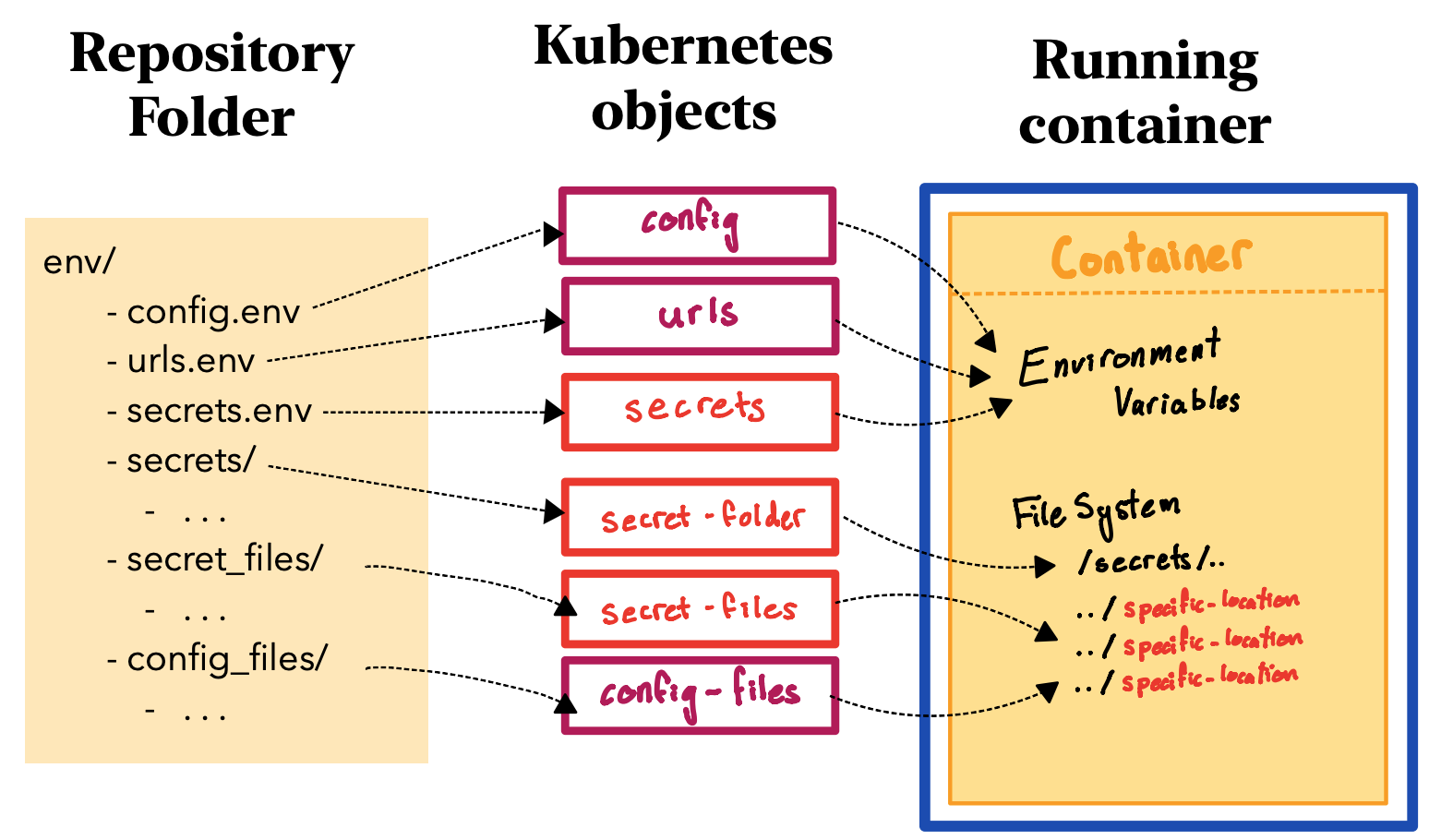
This section shows you how to view and update ConfigMaps and Secrets. It doesn't go into how the process of associating these objects with the container, as this has already been done. If you need to add a new file to a specific location, you'll need to contact the Kubernetes admin.
Where things are
Each repository is associated with these three objects:
deployment-config: A ConfigMap with generic configuration data. Loaded into the container as environment variables.deployment-urls: A ConfigMap with all the URLs used by the repository. Loaded into the container as environment variables.- At least one of
deployment-secretsordeployment-secret-folder: A Secret with all private data used by the repository. Loaded into the container as either environment variables, or the/secrets/folder.
These will be familiar to you as the config.env, urls.env and secrets.env files you made while preparing your repository.
If your repository includes any config files that need to be mounted at specific locations within the container, these are contained in the deployment-secret-files Secret (encrypted) or the deployment-config-files ConfigMap (not encrypted).
Listing All ConfigMaps
You can see all ConfigMaps in a namespace with:
| Name | Data | Age |
| graphql-config | 32 | 27d |
| graphql-urls | 13 | 27d |
| ui-config | 12 | 27d |
| ui-config-files | 1 | 27d |
| ui-urls | 2 | 27d |
And all Secrets:
| Name | Type | Data | Age |
| graphql-secrets | Opaque | 1 | 27d |
| graphql-secret-files | Opaque | 5 | 27d |
| ui-secrets | Opaque | 1 | 27d |
Viewing ConfigMap Values
It's often very helpful to know what the current configuration settings are. Whether you're debugging, fine tuning, or cross referencing for another repo; you'll need to do this at some point.
With ConfigMaps, this is pretty straightforward once you know the CONFIGMAP_NAME. One way to do get the values is:1
Namespace: staging
Labels: none
Annotations:
Data
====
HTML_SERVER:
----
https://myserver.com
IMAGE_SERVER:
----
https://myimages.com
Personally, I prefer just getting the full ConfigMap specification, because I think the output looks nicer:
data:
HTML_SERVER: https://myserver.com
IMAGE_SERVER: https://myimages.com
...
If you're looking for a specific value in a large ConfigMap, I recommend using grep or findstr to pull out just that line.
Viewing Secret Values
Secrets are base64 encoded at rest. You can view them in the same way as you can view configmaps. However, to get the true value of the secret, you will need to base64 decode the returned value.
data:
API_KEY: cGVzUwR0RCZUJ3RTdHelk0aUlFVno5
DATABASE_KEY: KILoki899990XEDFeri
UNIVERAL_ANSWER: XLII
...
Adding and Updating Values
To add or update values in a ConfigMap, use:
To do the same for a Secret:
You can verify this worked using the steps described above. To apply the changes to your running Deployment, use:
This will take a minute or two to finish.
IMPORTANT: This will not work for files that need to be mounted to a specific location inside the container. Talk to Hebe about these ones.
(value_1, key_2). Just read it carefully. ↩